Phishing has become the most common word in the cyber dictionary today. Everyone else is a victim of the phishing attack. This is indeed devastating, causing huge personal and financial losses. Cyber attackers are constantly looking for new ways to exploit. According to phishing email statistics, 1.2% of all the emails sent are malicious.
Even though the tech is advancing with anti-virus protocols, the best detection technology, and more, the complexity of phishing scams is severe. Thus, it becomes difficult to spot one. We can, of course, take into consideration the best practices and strategies to mitigate and avoid them. There are different ways in which phishing attempts take place, such as email phishing, SMS phishing, whale phishing, clone phishing, and more.
This blog guide focuses on the phishing attempts taking place through email and how you can identify and avoid them for a secure future.
With no further ado, let’s head over to the main topic.
Understanding What is Phishing
“Phishing” is essentially an attempt to steal sensitive or essential information from a user, such as personal details, bank account numbers, credit card details, contact numbers, and more, to use it for malicious purposes or sell the information obtained.
This is achieved by tricking the user into believing it comes from a legitimate source, when in fact, a bad actor is sending it. Phishing messages can be sent through various mediums, including emails, texts, social media, and others.
Let’s understand in short with an easy example how a phishing attempt works:
Suppose you get an email from a bank that you usually do transactions with. You receive an urgency email saying,” Your account needs immediate action,” or “click here to avail the credit card,” or click on the link to get a bonus of Rs 5000.”
These are some examples that scammers usually use to trick users and make them victims of a phishing attack.
The following are some of the scenarios that will help you identify phishing scams clearly:
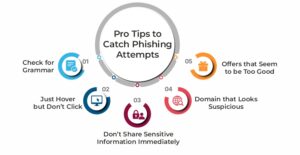
Top Ways to Identify Phishing Attempts
1] Check for Grammar
One common way to spot phishing attempts is by checking for typos in the message. Attackers are often less focused on the grammar side. If you find any mistakes in the email or message, please understand that the email is suspicious.
2] Just Hover but Don’t Click
Don’t randomly click on the link. Double-check twice if the alt text matches the display text. If it’s not similar, strictly avoid clicking on the link.
3] Offers that Seem to be Too Good
Be aware of the messages that create excitement in the subject line itself. This is regarding an offer that you can’t resist going with. But it might be a scam. You need to check for the following points:
- Comes from a source that doesn’t provide such reasonable offers
- Offers something in return or nothing
- Alongside, an email or SMS that asks you to click on the link to avail the offer
Here are a few examples:
- You can now earn money online, working from home
- You are eligible for a gift voucher
4] Domain that Looks Suspicious
Official emails always come from a reputable domain. However, if you get emails from unknown or public domains, this can be a sign of phishing. Here are a few scenarios mentioned:
- Email from public domain, [email protected]
- The email addresses contain unusual special characters
- Typo mistakes in the domain name
5] Don’t Share Sensitive Information Immediately
A phishing attempt email usually asks you to share sensitive information such as your contact number, email, name, address, etc. No bank will ever ask you for these details—double-check before sharing them.
Steps to Avoid the Phishing Attempts
1] Conducting Phishing Attempt Tests
Phishing attack testing is a crucial part of preventing your organization from phishing scams. The overall security in the organization can be improved by training your employees in identifying phishing SMS and emails. Thus, you can carry out periodic tests, alongside testing for flaws, and having an effective response plan can help reduce the chances of a phishing attack.
2] Keeping a Close Eye on Your IT Infrastructure
Organizations must regularly scan their infrastructure to identify flaws and vulnerabilities. The company should adhere to all security policies and standards to prevent sudden mishaps.
3] Update Your Software
Make sure to be updated with the latest operating system and software. Bad actors can often exploit outdated devices. So, make sure to patch the vulnerabilities and stay updated with the latest security patches.
4] Train Your Team
The most important part of being away from the phishing scams is educating your teams. Conduct a phishing awareness program in your organization to help employees recognize the signs of phishing before it's too late. This way, employees can spot the phishing attack and stay vigilant.
Wrapping it Up!
The cyber world is creating new forms of attack each day, with phishing being the most common, as stated above. However, to prevent this, you need to follow specific measures and stay safe online. Otherwise, hackers are here to cause you trouble and crush your reputation. I hope the above blog has clarified your understanding of the phishing attempt!
Our site is 100% committed to publishing cybersecurity-related content. Check it out now!
FAQs -
1] Which are the most common types of phishing attempts?
Ans: Some of the common types of phishing attempts are email phishing, spear phishing, SMS phishing, angler phishing, etc.
2] How can I identify phishing emails?
Various signs can help identify phishing, including unusual domains, suspicious links, urgent messages, and grammatical errors in emails or texts.
Recommended: AI Email Security Solutions for Businesses