Cyberthreats are growing at an alarming rate! This recent remote code execution (RCE) security flaw, tracked as the 7-Zip RCE (CVE-2025-11001), affected 7-Zip and has currently not observed active exploitation in the wild, according to the advisory shared and updated recently by NHS England. 7-Zip is a widely used, open-source, free file archiver.
The newly emerged threat puts millions of users at risk. Nevertheless, it is important to understand the complete security flaw, alongside who can be affected by these attacks, and the preventive measures for anyone using 7-Zip. This blog covers everything for you!
What Is CVE-2025-11001?
CVE-2025-1101 is a security flaw that allows remote attackers to execute arbitrary code on installations of 7-Zip. The specific flaw lies within the handling of symbolic links in the Zip files.
By crafting malicious Zip files with symlinks, attackers can disrupt the intended extraction folder and traverse to unintended directories. “An attacker can utilize this vulnerability to execute code in the context of an elevated user/service account, or a machine having developer mode enabled, “stated the security researcher Dominik, (aka pacbypass), who released a PoC.
Alongside this, he also mentioned that the security vulnerability affects 7-Zip versions 21.02 to 24.09 when converting symbolic links from Linux to Windows. Moreover, it can be exploited on Windows systems.
Why is the 7-Zip RCE flaw (CVE-2025-11001) Dangerous?
The 7-Zip RCE flaw (CVE-2025-11001) requires user interaction, such as opening or extracting the malicious Zip file. Here, the execution path becomes dangerous when 7-Zip is run by service accounts or systems with elevated rights.
The security researcher, Dominik, aka (aka pacbypass), came up with two important points:
- As mentioned above, the vulnerability can only be exploited on Windows
- Alongside, it can be exploited from the context of a service account or when developer mode is enabled
The conclusion is that everyday desktop users are at risk. Moreover, organizations that run 7-Zip in automated systems or services are highly vulnerable.
Who is Most Likely to be Affected by (CVE-2025-11001)?
Anyone using 7-Zip is at potential risk, whether an individual, a techie, or a large-scale organization, who downloads and extracts archives from untrusted sources. The following are some of the scenarios:
- Generic users who save files, images, and more on their device and download them in ZIP format.
- IT professionals who deal with many archived files, system backups, and more.
- Windows systems with developer mode enabled
- Organizations where 7-Zip operatesunder service accounts.
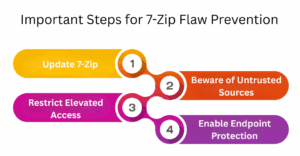
What Steps Should Users Incorporate for Prevention?
- Update 7-Zip:All 7-Zip users need to download the latest patched version.
- Beware of Untrusted Sources: Don’t randomly download or extract archives from untrusted or malicious sources.
- Restrict Elevated Access: Do not run 7-Zip with unnecessary elevated access.
- Enable Endpoint Protection: Modern EDR solutions detect and block suspicious symlinkor file-write behavior.
Ending Thoughts
A security-first approach is a must-have in today’s cyberthreat landscape. The recently exploited 7-Zip RCE flaw (CVE-2025-11001) poses a significant risk to users. As active exploitation is already underway and the PoC code is easily accessible, the latest version of 7-Zip is not only highly recommended but also necessary.
Those organizations using older versions are at greater risk in automated or privileged settings. The most appropriate counter to this new threat is quick mitigation and user awareness.
We bring all the latest blogs around the cybersecurity landscape! So, make sure you don’t miss out! Visit our site now.
FAQs
1] Which versions of 7-Zip are affected by this vulnerability?
Ans: Mainly, the 21.02 to 24.09 versions have been vulnerable to this attack.
2] What do you mean by directory traversal?
Ans: Directory traversal means an attacker can create a malicious Zip file with all the symbolic links pointing outside the intended extraction folder.
Related reading:
Key Pillars of Google’s Vulnerability Management System
Google Chrome Zero Day Vulnerability: All You Need to Know About
VoIP Security Vulnerability and Best Practices for Safer Communication