They say ‘data’ is the biggest asset for businesses these days. So, it’s essential to safeguard something so important and keep it out of the wrong hands. But how will you protect your digital assets from something you cannot see? That’s where cybersecurity comes to play.
Now, you might feel relieved because you have certain antivirus software installed in your systems. Well, cybersecurity does not end with installing an antivirus. It comprises of multiple layers and functions that create a 360° shield for your system.
It may seem that cybersecurity in present times is a small sector of the market, but the rise in the global cybersecurity workforce is estimated to be 4.7 million professionals, showing an evident significance of the sector. On the other hand, cybercrime is estimated to cost over $23 trillion by 2025.
Defining Cybersecurity
Cybersecurity is all about combining multiple functions to fight cybercrime and protect all systems, data and networks. It aims to stop unauthorized access, prevent hacking into private systems, and protect against data breaches. Cybersecurity is also referred to as ‘Electronic Information Security’ or ‘Information Technology Security’.
It involves all the practices and technologies designed to safeguard all systems, private files, confidential data and customer information from being leaked or disclosed. Such breaches may lead to grievous losses, legal concerns, and privacy issues.
The Foundation of Cybersecurity
Cybersecurity incorporates various fundamentals to curate a strong foundation. Have a look at some of the major fundamentals:
- Confidentiality: Maintaining limited authorized access to prevent disclosure or misuse
- Integrity: Protect from unauthorized access to avoid manipulation, deletion or modifications
- Availability: Ensuring is it usable by any authorized user any time
- Threat Identification: Forecasting potential loopholes and reduce weak spots
- Risk Mitigation: Enabling effective cybersecurity practices and technologies
- Rapid Response: Maintaining backup and immediate detection and recovery of lost files
Common Threats that Compromise Cybersecurity
Cybersecurity threats are dangerous actions carried out by skilled individuals who aren't authorized to access systems. Their goal is often to hack, steal, damage, manipulate, or delete information, leading to significant losses for businesses.
Over the years, the industry has witnessed a significant rise in these threats and cyber-attacks, making it more crucial than ever to prioritize cybersecurity in present times. We have listed down some common threats that may compromise your cybersecurity system:
Data Breach: Data breaches are one of the biggest cyber threats out there. It's a harmful practice that can result in the deletion, manipulation, or even exposure of sensitive information to the public or competitors.
Malware: You’ve probably heard the tale of the Trojan Horse, right? Well, Malware attacks are quite similar. It's when sneaky, harmful software disguises itself as an app, an email attachment, a tempting promotion, or a user log onto an infected website and weak networks to enter the system and cause harm. It releases viruses in your system.
Social Engineering: It’s possible that you’ve received some suspicious calls, texts, or emails pretending to be from your bank, asking for personal information or bank details. This is a classic example of social engineering, where someone tries to trick you into giving away sensitive information or access.
Hackers: Skilled individuals known as unethical hackers can infiltrate your system by exploiting vulnerable network or cracking weak security measures and passwords. This gives them direct access to private files and internal systems.
It is necessary to make consistent efforts towards cybersecurity in present times. Businesses can keep an eye on IoCs (Indicators of Compromise) to spot any security breaches or potential threats. These indicators can include things like sudden unusual traffic, system slowdowns, suspicious errors, and unauthorized attempts.
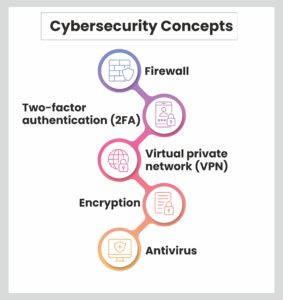
Explore the Various Cybersecurity Concepts
Cybersecurity in present times is not just a minor IT tool, but a complex subject. It comprises of multiple concepts that create different layers of protection. It is made up of key components that strengthen the protective barrier. Let’s go through a few concepts below:
Firewall: It acts as a security wall between the internal network and the external world, working as a filter for any unauthorized traffic.
Two-factor authentication (2FA): This function adds an extra layer of security by asking users to present two forms of identification before gaining access to an account or system.
Virtual private network (VPN): A VPN creates a safe connection that allows users to browse the internet or access a private network with confidentiality by hiding the IP address of the user.
Encryption: It is the process of transforming data into a secure code, keeping it safe during transfers or when stored.
Antivirus: Think of antivirus software as your digital guard, designed to spot, prevent, and eliminate harmful software. There are multiple antivirus software available in the market to strengthen cybersecurity in present times.
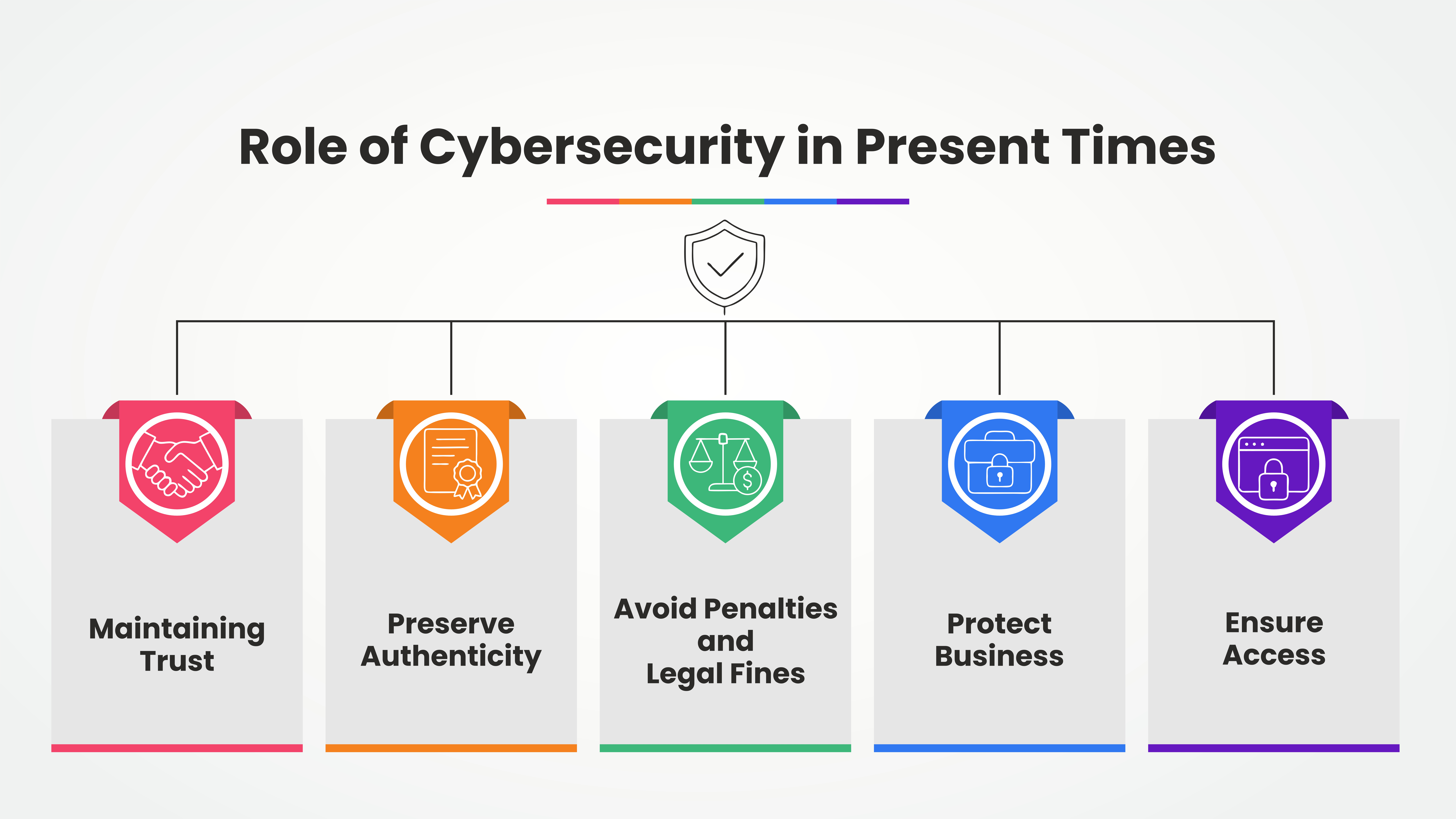
Role of Cybersecurity in Present Times
From small businesses to huge multinational organizations, cybercrime has become a major threat globally. The significance of efficient cybersecurity practices is on the rise. Following are the reasons justifying the importance of cybersecurity:
Maintaining Trust: Customers share their personal information with any business due to the trust and expect them to protect it. If in any circumstances the information gets leaked, it leads to deteriorating trust and a bad reputation.
Preserve Authenticity: Hacked systems give access to external parties who may manipulate or delete data affecting the authenticity of the data.
Avoid Penalties and Legal Fines: Every business is under obligation to comply with several regulations and legal frameworks; any non-compliance may lead to legal issues and fines.
Protect Business: Cybersecurity creates a barrier between the internal network and unauthorized outsiders who may harm business operations in multiple serious ways.
Ensure Access: Cybersecurity aims to create a limited network of authorized people and ensures only they have access to safeguarded information.
Challenge to Cybersecurity Globally:
We're talking about leaked confidential data, exposed private information, financial losses, hacked systems, damaged reputations, criminal offences and the list goes on! The increasing frequency in cybercrimes has made every business alert.
- The private data of 700 million LinkedIn users (around 90% of LinkedIn users) was offered for sale by a hacker, back in June 2021.
- The average cost of a serious cyber-attack stands at $4.4 million, revealed by PwC's digital trust survey revealed. Surprisingly, 36% of those surveyed admitted that their organization had experienced a data breach, racking up costs exceeding $1 million over the last three years.
- In 2016, Uber faced a cyber-attack that exposed private data of 57 million customers, it not only damaged their reputation but also led to breaking a Pennsylvania law.
Future of Cybersecurity!
The experts of the industry anticipate the incorporation of AI and IoT sensors for early detection of threats and potential cyberattacks. Businesses are planning to adopt 5G network security, Zero Trust Models, Cloud Security and similar models to curate different types of layers to protect the system, data and network from every dimension.
Cybersecurity in present times is an evolving and growing sector with new challenges and technologies developing every day. It opens gates for multiple technological revolutions and career opportunities.
Make sure to subscribe to SecureItWorld for many more tech-oriented and insightful blogs!
Explore More:
What is the Role of Artificial Intelligence in Cybersecurity?
Importance of Cybersecurity Training: How Businesses Can Prepare Employees to Combat Emerging Threats