Cybersecurity is a top priority for individuals and organizations today. The data we generate every day is at high risk, as cybercriminals are continually seeking ways to exploit it. Under such circumstances, adopting resilient security strategies is important.
Privileged access management (PAM) can be highly advantageous in this regard. Sources state that over 91% of organizations have integrated PAM strategies to strengthen their security framework. In this blog, we’ll learn about PAM thoroughly, understand its importance, and assess privileged access management use cases.
What is Privileged Access Management?
Privileged access management (PAM) is an identity-based security strategy that combines monitoring, detection, and prevention of unauthorized privileged access to sensitive business resources. It includes people, technology, and processes to identify privileged accounts and authorize access. PAM safeguards organizations and their assets from devastating cyberattacks, restricting malicious access requests.
Primarily, PAM recognizes the people, processes, and technologies within an organization that require privileged access. The framework then determines specific policies to protect critical assets from vulnerabilities. Centralized credential management, session monitoring and reporting, strict access control, and secure credential storage are the essential elements of privileged access management.
While meeting its goals, PAM incorporates the following stages:
Privileged account management: It is the primary stage of PAM where accounts with secured permissions are created and authenticated.
Privilege management: Here, the users eligible to get privileges are assessed, and the process of managing their privileges is determined.
Privileged session management: In this phase, privilege is monitored, and suspicious activities are detected for uninterrupted compliance.
There are different types of privileged accounts that ensure appropriate and unrestricted accessibility of files and other resources. Service accounts, domain administrator accounts, business privileged user accounts, emergency accounts, and local administrator accounts are the common types of privileged accounts.
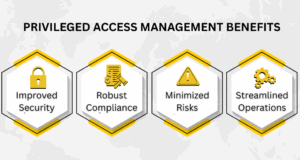
Privileged Access Management Benefits-
At its core, privilege access management helps organizations identify potential access threats and eliminate them. Effective privileged access management use cases demonstrate how the process enhances firms' security strategies while safeguarding their resources from both internal and external threats. Here are the key benefits of PAM to look after-
Improved Security: PAM helps in fortifying the overall security infrastructure of an organization. It not only helps eliminate unauthorized access but also protects company assets from internal risks, such as insider attacks.
Robust Compliance: The access controls implemented by PAM also help organizations remain compliant with global privacy benchmarks such as GDPR, HIPAA, and PCI DSS.
Minimized Risks: PAM helps significantly identify possible data breaches and cyber risks. Alongside that, it enables continuous monitoring, allowing companies to detect compromised user accounts and implement appropriate risk mitigation measures.
Streamlined Operations: Advanced access management also enables organizations to operate with minimal disruptions. Moreover, it reduces the requirement for complex access management methodologies.
Privileged Access Management Use Cases:
PAM can be implemented and utilized for different purposes. Here are the top privileged access management use cases-
Reduce Insider Threats:
Insider threats have become a major risk for organizations across the globe. Privileged access management helps address such risks by appropriately distributing access. PAM integrates account discovery abilities while allowing firms to automatically detect new access requests and unmanaged privileged accounts, ensuring authenticated access to files and resources of a firm.
Secure Remote Access:
Remote and hybrid modes of work are on the rise in recent times, which can also cause data breaches. PAM establishes a safe and controlled access management framework that keeps suspicious accounts away from sensitive files and resources. Alongside that, PAM strategies unlock real-time visibility, monitoring, and recording remote accessibility sessions. So, firms can easily track who is accessing which file and for how long.
Safeguard Cloud Environments:
Since companies are using cloud computing significantly, cloud servers have become an easy target for cyber attackers. Hence, it is crucial for firms to protect their cloud servers from risks. PAM enables companies to allow access to verified and privileged accounts only. Additionally, PAM-driven continuous monitoring allows security teams to track who is accessing which files in cloud servers from where and for how long.
Manage Third-party Vendor Access:
Third-party service providers often need to access sensitive information from organizations. Ineffective management of such approaches can cause devastating risks. PAM incorporates strict access control alongside continuous monitoring and audit, while sharing information with third-party vendors. It further enables time-bound accessibility to ensure data retrieval and usage, adhering to the company’s guidelines.
Sustain Security and Compliance:
Alongside offering sophisticated opportunities for security, PAM offers advanced compliance parameters so that your firm adheres to the global security guidelines. Since compliance with privacy guidelines such as GDPR, HIPAA, and PCI DSS requires strict control and monitoring, PAM enables these for privileged access. Alongside that, PAM supports continuous auditing, which not only helps trace security and compliance gaps but also helps address them.
Concluding Remarks!
Security and privacy are two crucial elements for organizations nowadays. Inefficient privacy strategies can lead to data breaches and cyberattacks. Privileged access management is a result-driven methodology that strengthens the overall security infrastructure through advanced access management and compliance tactics.
The above-mentioned privileged access management use cases describe how the strategy can offer a holistic approach to safeguard your organizational resources and files from threats.
Want to catch up with emerging technologies and practices? Dive into our in-depth blogs!
F&Qs:
Q1. What is privileged access management used for?
Answer: Privileged access management is used to control and secure accounts with advanced access to protect files and resources from threats within an organization.
Q2. What is the difference between PAM and IAM?
Answer: Privileged access management (PAM) enables sophisticated access controls for privileged accounts with advanced permissions. On the other hand, identity and access management (IAM) controls user access based on their roles.
You May Like:
Understanding Threat Intelligence and Its Importance for Advanced Security