In recent past, the focus on development of security controls has taken an upward trajectory to manage the increasing mobile phone intrusions and security threats; like anti-virus and firewalls that are currently fiscally available. As the functionality of the mobile increases, a desire for sophisticated and better security controls like the Intrusion Detection System is at an all-time high.
When an attacker gets an illegitimate entrance into a mobile phone, network or system, it is termed as Intrusion. Cyber criminals, with the help of advanced techniques, infiltrate organizations without getting exposed. Doing so, they can cause harm to the targeted individual in ways that are dangerous, like identity theft, financial theft, loss of data and credentials, etc.
The Intrusion Detection System (IDS) was created to address this problem. In this blog, we breakdown the ways mobile phone intrusions take place and the methods for detecting them.
What is Intrusion Detection System?
Intrusion detection system (IDS) oversees the network traffic for malignant transactions and notifies the owner when these activities are observed by the system. All of these violations or illegal activity are either communicated to the administration as an alert or are centrally logged in a SIEM system. IDS protects a network from intrusions and monitors it for illicit activity. The intrusion detector's learning job is to develop a prediction model that is powerful enough to distinguish between good or normal connections and poor connections, such as intrusions.
How does the Intrusion Detection System Work?
Let’s understand this in a simple step wise patten.
- An IDS supervises the traffic on the computer to identify any skeptical activity.
- Analysis of the information flowing through the network to intercept and search for the patterns and signs of suspicious activity.
- The IDS would then compare the activity traced on the network to the prearranged sets of guidelines and patterns to find out any activity that might suggest an attack or intrusion.
- If the system detects any malicious behavior that corresponds with the pattern that has been set in the system, an alert is issued to the administrator.
- Now the administrator investigates the alert received to take appropriate action to steer clear of any damage or any further intrusion.
Importance of the Intrusion Detection System
The number of mobile phone intrusions has increased lately, so, having an extra layer of security was never a disadvantage. IDS works with other defense tools to identify and apprehend the threats that may leap over your main defenses. If your principal defense misses out on defending a threat, then IDS will alert you.
What should be the correct placement of IDS?
The ideal position for the IDS placement to defend against mobile phone intrusions is at the rear of the firewall, which is also the most common position for an IDS to be placed. Keeping the IDS behind the firewall helps the IDS with better conditions for visibility of the approaching network traffic and would not get the traffic between users and network.
Using the signature-based detection method, an IDS will keep an eye on OSI model surfaces four through seven. If the total number of aimed breaches is shown rather than the actual breaches that pulled through the firewall, it will take less time to identify successful assaults on the network or system.
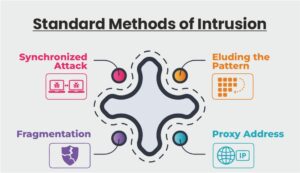
Standard Methods of Intrusion
To outsmart the IDS, cyber criminals carry out attacks in various methods which give them undue advantage. We list the various standard methods of mobile phone intrusion.
- Synchronized Attack – Making use of multiple attackers to scan a network, bewildering the IDS and puzzling it to understand what is actually happening.
- Eluding the Pattern – Using variable or erratic methods to attack and to escape from the detection of IDS which follows certain patterns to identify threats.
- Fragmentation – Data is sent in fragments to cruise past the detection system.
- Proxy Address – With the use of non-secured proxy servers, the source of attack is hidden, making it challenging to determine the attacker.
How Useful is an Intrusion Detection System?
- Detection of suspicious activities – IDS detects malicious actions and alarms the system before any major harm occurs.
- Better Network Performance – IDS can identify any network performance problems and fix them to enhance network performance.
- Requirements for the Agreement – Meeting the compliance requirements for the correct following of the rules and regulations by surveillance of network activities and generating reports.
- Provision of Insights – For the improvement of any system, the analytic report of the whole procedure is crucial. IDS provides insights into the network traffic which can then be used to find any weaknesses and provide the path for the improvement of the system further.
Challenges of the Intrusion Detection System
Unfounded Panic – False alarms can be generated for harmless activities which can cause unfounded panic and needless concern.
Use of Resource – IDS uses system resources in ample amounts, likely slowing down the overall performance of the network.
Management Issues – The set up and management of the IDS is complex in nature requiring specialized skill sets with knowledge to operate.
Maintenance – Tuning and regular updating is required for the effective performance of the IDS, which is a time taking action.
In an increasingly digital environment, efficient techniques for identifying mobile phone intrusions are crucial for protecting user privacy and personal data. People and organizations can strengthen their defenses against the increasing risk of mobile security breaches by putting strong detection methods into place.
To learn further about security, visit SecureITWorld!
Recommended Reads:
Safeguard Your Device: Mobile Security Apps
How to Secure Your Mobile Devices? Know the Top Tips
Comprehensive Mobile Device Security: Safeguarding Your Digital Life