Imagine you turn on your computer, expecting to start your day, but instead of your normal screen, a big, frightening message pops up. It says, "All your photos, documents, and work files are scrambled and locked up! If you want them back, send us money-a ransom-in digital currency right now."
That is the scary reality of a ransomware attack. It is not just a technical problem, but it is like having a digital thief break into your house, locking up all your valuables in a safe, and holding the key for ransom until you pay up.
It is a special kind of bad software created only for one thing: making money by scaring you. It doesn't usually erase your files; it uses super-strong encryption, which means a high-tech lock, to make them completely unusable. Learning how the bad guys get in is the first step to keeping your digital life safe. Let's break this threat down and learn simple steps you can take to protect yourself.
What is Ransomware?
Ransomware attack is a kind of malware, short for malicious software. While many other viruses corrupt or destroy files, ransomware is all about extortion. It does not destroy the data immediately; rather, it locks the data with powerful encryption to make it entirely unreadable and unusable. The key for unlocking it is held by the criminals.
- The Problem: It is a bad program, what we call malware, that gets onto your computer or network surreptitiously.
- The Action: Once inside, it quickly uses a very powerful code lock called encryption on all your important files, such as your business spreadsheets, family photos, and customer lists.
- The Demand: Then, it flashes up a ransom note, demanding payment for sending you the unlock code in hard-to-trace money, such as Bitcoin.
Why Are These Attacks So Common?
Easy Money for Hackers: Hackers ask for payment in digital money like Bitcoin which allows criminals to get paid quickly. Also, the transactions are very difficult to trace by the police and governments.
They Target Important Places: These ransomware attacks target important places like hospitals, factories, and government offices. Such places that need their data to keep working. These places pay the ransom just to get back to normal.
Double Trouble: Modern attacks are particularly nasty. Before locking the originals, they steal a copy of your sensitive files, after which, they threaten to post all your private data online unless you pay for the key. This is what is referred to as the "double extortion" trick.
The Cost is Huge: Ransomware attacks can cost a lot of money. The FBI says they are one of the most expensive types of online crime. But it’s not just about money. When a hospital is attacked, it can delay important treatments and even life-saving surgeries. This shows how serious and harmful these attacks can be in real life.
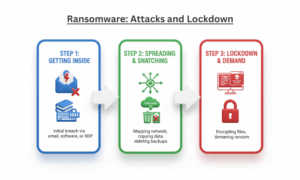
Ransomware: How It Attacks and Locks Everything
A ransomware attack does not happen suddenly. Rather, it is a quiet and multi-step plan.
Step 1: Getting Inside (The Entry Point)
They need a way through your digital door.
- The Sneaky Email: You receive an email that looks like it is important, perhaps from a delivery service or a utility company, that puts pressure on you to click a link or open a document. If you click, the nefarious program is loaded onto your machine in an instant. (Note: Always verify the sender's actual email address!)
- Old or Unpatched Software: If you have not updated your Windows or Chrome browser for quite a while, it could have well-known security "holes." The attackers scan the internet all over, looking for these specific holes to push the ransomware straight onto your system.
- The Unlocked Backdoor: Many businesses use a way to let people work from home called RDP, or Remote Desktop Protocol. If the password for that is weak, hackers can easily guess it and just walk right into the company network as if they were an employee.
- The Twist: Nowadays, criminals also attack smaller companies that deal with bigger ones, like a supplier or a vendor. They use the small one as their weak point to penetrate the network of the major target.
Step 2: Spreading Out and Snatching (Set Up Camp)
It does not attack immediately. It is sneaky and intelligent:
- Mapping the Territory: It starts by moving quietly around your computer or company network in search of the most valuable files and where your backups are located.
- The Silent Steal: Before it locks anything, it makes a copy of all your private data, customer lists, secrets, etc., and sends that copy to the hackers' computers. This is for the double extortion threat later.
- Destroying the Safety Net: It will actively try to delete or corrupt any backup copies you may have saved on your local network, so you won't be able to restore the files yourself.
Step 3: Lockdown and Demand
- The Files Are Gibberish: The software uses its high-tech lock (encryption) on everything. You see the file names, but when you try to open them, some code shows up, and you are unable to open the file.
- Then there is the notice: A pop-up shows up or a document appears in every folder, informing you that your files have been locked and demanding you pay the ransom within a certain amount of time.
What to do to Protect Your System from such Ransomware Attacks?
You can stop these ransomware attacks before they ever start. Your defense comes down to a few simple, steady habits.
Your Lifeline: Back Up Your Files
This is the first thing to do. Make it a practice to take a backup of your files once you are done with your work. If the worst happens, and you have a clean backup, then you can just wipe your computer clean and restore your files, completely ignoring the criminals.
- The 3-2-1 Rule: Three copies of your most valued data (on two different types of storage, one of which is a cloud service or a hard drive) and at least one completely offline storage (unplugged) is the best one.
- Keep It UNPLUGGED: The critical point is that once you are done with your backup, you need to physically unplug the external drive from your computer. If it stays plugged in, the ransomware can find and lock those backups too!
Be a Skeptic, Not a Clicker
Most ransomware attacks depend on you making a mistake. Be suspicious of every surprise email.
- Slow Down and Check: If an email is urgent or too good to be true, it is probably fake. Look very closely at the sender's email address, not just the name. Is there a tiny typo in the company name? Delete it.
- Use Your Mouse: If you hover your mouse pointer over a link (don't click!), the actual website address will pop up. If it looks strange, do not click it.
- Say No to Macros: If a file, like a Word doc, asks you to "Enable Content" or "Enable Macros" just to see it, close the file now! That is how the bad program gets started.
Keep Your Digital Locks Fresh
Security updates are like repairing broken windows on your digital house.
- Enable Automatic Updates:Turn on automatic updates on the operating system and all applications. That includes Windows, Mac, Chrome, Adobe, and others. These updates close the known holes that hackers look for.
- Use Extra Security: MFA, or Multi-Factor Authentication, activates security on all important accounts, from email to banking. MFA requires a code after the password from your phone and stops a hacker from using a password obtained by them in order to access and then launch ransomware attacks.
- If the Worst Happens: What To Do If you do see that terrible ransom note, the best advice is not to pay the ransom. There is no guarantee that you will pay the money and receive a key or that it actually works.
- You Fund Crime: Paying only encourages and funds the criminal groups to strike at more individuals. Instead, take these steps immediately:
- Disconnect Fast: Immediately disconnect the infected computer from the internet and the network. This halts any further spread of the ransomware to other machines.
- Call to Action: Notify your company's IT or security professional immediately. If serious, report the crime to law enforcement authorities like the police.
- Restore: Bring your data and system back online with the use of your clean, offline backup.
The thing is, ransomware attacks are a grave threat, but by just instilling simple smart habits, especially a reliable, disconnected backup and a healthy dose of suspicion against email, you can protect yourself and be one step ahead of the digital thieves.
Final Words!
Ransomware attacks are a part of the digital world we live in, but they are not ones we must passively accept. The key to all this is adopting smart habits, prioritizing backups, and being vigilant. We can all become a powerful part of the line of defense and make the digital world a safer place for ourselves and our businesses.
Check out SecureITWorld for more information!
FAQs
Q1. What is the root cause of a ransomware attack?
Answer: Ransomware attacks happen when an individual clicks on a suspicious link or opens up a phony email. This allows a hacker to enter the system.
Q2. What are the steps in a ransomware attack?
Answer: There are three steps of a ransomware attack:
- Hackers break in
- Lock your files
- Then demand money to unlock them.
Q3. Can ransomware be removed?
Answer: Yes, it can be removed. Sometimes files cannot be recovered unless you have backups or expert help.
Recommended for you:
5 C’s of Cybersecurity – Strategies for Business Owners to Eliminate Cyber Attacks
What is GhostGPT? Will it Enable More Devastating Cyberattacks?
Understanding DDoS Attacks? How do they Disrupt Service Availability