Even though cybersecurity has become a top priority for businesses, devising and implementing a robust security framework has remained a far-fetched dream for many. Common challenges include a lack of knowledge, an absence of a strategic approach, and prioritizing quantity over quality when integrating security strategies.
Data reflect that among organizations that integrate cybersecurity practices, the majority fail to sustain it with a long-term vision. Over 38% of businesses worldwide have no cybersecurity budget. 57% of operations teams across companies do not follow the best security practices. Additionally, 62% of teams do not aim to improve security.
Such stats show how companies fail to strategically plan their cybersecurity approaches and, as a result, experience data breaches and operational disruptions. In this blog, we’ll learn what the cybersecurity paradox exactly is and the cybersecurity best practices to aim for a resilient future.
Understanding Cybersecurity Paradox
The cybersecurity paradox describes a mismatch between the security goals of organizations and the strategies they adopt. Firms recognize cyber risk as a top business threat, yet security too often sits outside strategic planning, underfunded or delegated to IT teams alone.
In practice, this means that decision-makers and boards within firms acknowledge the potential risks posed by cyber threats. However, their roadmaps and budgets still prioritize short-term growth over long-term resilience. As a result, vulnerabilities persist even as organizations ‘we’re protected.’
The paradox often takes place when organizations rely on multiple tools and approaches to strengthen their security framework. This often creates complexity among employees, disrupts accessibility within the organization, and ultimately fails efforts. In simple terms, the cybersecurity paradox describes the futile attempt of companies that understand the importance of resilient security strategies but fail to adopt appropriate tactics.
How Can Cybersecurity Paradox Create Difficulties for Your Business?
That disconnect between the security objectives and strategies implemented has real, cascading consequences. The foremost drawback that takes place is tool sprawl, piling on point solutions. Each promising to fix one gap creates complexity, blind spots, and integration of challenges that increase operational risk rather than reduce it. Attackers exploit those seams, using automation and advanced tactics to find weak links between systems.
Second, poorly measured ROI. When protection succeeds, ‘nothing happens’ makes it hard to justify continued spending. When the approach fails, the business pays downtime, fines, and reputational damage. Thirdly, the challenge of innovation friction arises. Security seen as a blocker leads product teams to bypass controls, increasing shadow IT and expanding the attack surface. These dynamics show why adding more products without architecture and governance can make an organization less secure.
AI has become a key technology for companies to strengthen their cyber defenses, yet it can be a double-edged sword. AI can surely help in implementing automation in the cybersecurity framework. But depending entirely on AI models can also lead to devastating outcomes. Vulnerabilities in AI models fascinate cyber attackers the most. As a result, security goals stay unmet, creating a situation of paradox.
Cybersecurity Best Practices to Overcome Paradox:
Robust cybersecurity requires strategic planning and a distinguished budget. Additionally, companies must overcome the myth that cybersecurity is the responsibility of only IT professionals. While integrating security strategies, primarily organizations have to ensure their appropriate awareness.
Alongside, analyzing effective adherence to the implemented security policies and practices by every team is a key consideration. Here are the cybersecurity best practices to follow-
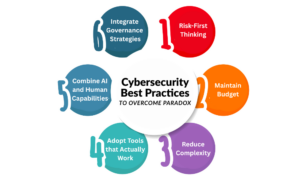
Risk-First Thinking: Cyber risks can occur at any time, causing great disruptions. Hence, it is crucial to stay threat-ready alongside preserving a risk-first mindset. Notably, human error has been a key cause of cyber breaches, which can be caused by employees of an organization. So, scheduling training sessions to establish risk-first thinking across teams will be beneficial.
Maintain Budget: Alongside planning, cybersecurity needs significant investment. So, companies must maintain a yearly budget for the same. Free tools and processes may offer robust measures but a shorter period. On the other hand, cybersecurity is a continuous process. So, it seeks continuous investments and efforts.
Reduce Complexity: Cybersecurity approaches have to be simplified and easy to understand. Since every team in an organization is equally responsible for solidifying security practices, IT teams must aim to reduce complexity in the framework.
Adopt Tools that Actually Work: Integrating multiple tools can make the process complex. So, choosing appropriate tools that sustain standard security, scalability, resonate with your business goals, and help in attaining a long-term security vision will be beneficial for firms.
Combine AI and Human Capabilities: Implementing AI for security purposes is undoubtedly an innovative idea, but relying solely on AI models can lead to unintended outcomes. AI models need compliance and continuous monitoring. For this purpose, combining AI and human effort will help establish resilient frameworks.
Integrate Governance Strategies: It is crucial to continuously assess compliance and adherence with the enabled cybersecurity practices. It helps in understanding where the approach is failing, and which areas need improvement. Adopting advanced governance strategies can be highly beneficial for this purpose.
Quality Over Quantity: A Solid Cybersecurity Approach!
With cybersecurity becoming more or less a myth in the digital era, it is our responsibility to integrate strategies that protect our data from vulnerabilities, help build client trust, and drive long-term success. In this regard, focusing on quality over quantity of tools and strategies will benefit your business. A deliberate, quality-driven approach can surely take security from a cost center into a business enabler.
Quality means fewer, well-integrated controls that are tested and governed. Choose solutions that deliver measurable risk reduction and support transparent reporting to non-technical stakeholders.
Dive into our informative blogs to stay up to date on emerging cybersecurity practices.
FAQs:
Q1. What is the paradox of AI in cybersecurity?
Answer: AI solidifies cybersecurity practices alongside imposing remarkable security risks. This situation is known as the paradox of AI in cybersecurity.
Q2. What are the 5 main threats to our cyber security?
Answer: Malware, phishing or social engineering, DDoS attacks, insider threats, and SQL injection are the main threats to cybersecurity today.
Don’t Miss:
The Best Cybersecurity Checklist to Protect Your Data
Top 5 Open-Source Cybersecurity Tools You Can’t Afford to Miss
Exploring Cybersecurity Audit, and How Can It Benefit Your Business?