In today’s digital age, data privacy is a crucial topic that shouldn’t be overlooked. A report says that around 3.8 million records are prone to cybersecurity attacks each day. This is indeed an alarming sign! We depend on online platforms every moment, whether it's texting, shopping, or managing our finances through net banking and so on.
Do you ever wonder if your private data is safe?
You might be juggling with the thought! Moreover, encryption is one of the powerful security methods that keeps your sensitive information highly secured. Further, it can be accessed only by authorized users. Encryption converts readable text into unreadable text (ciphertext) that can be accessed only by authorized users with the decryption key. There are different types of encryption algorithms each with their own uniqueness and aimed at protecting data.
This blog explains all about encryption algorithms, their types and benefits.
Let’s get started!
What is Encryption Algorithm?
SMBs, big scale organizations, use this method to protect their sensitive data from hacker's trap. To put it simply, an encryption algorithm is a technique that transforms data into ciphertext. A special key is used to transform your data into a form that is scrambled.
It may appear to be random text, but it can be decrypted to its original form by a decryption key. This is important for keeping sensitive data from hackers and beneficial for individuals and organizations alike. As, encryption algorithms focus on data confidentiality, integrity and preventing business losses.
There are mainly two types:
1. Symmetric Encryption Algorithm:
This type of encryption technique encrypts and decrypts data using a single key. Symmetric encryption requires secure key exchange despite its efficiency.
2. Asymmetric Encryption
Here, a public key is used for encryption and a private key is used for decryption in asymmetric encryption, sometimes referred to as public-key cryptography. The public key can be used by anyone to encrypt data, but only the private key holder can decode and see the original data.
Types of Encryption Algorithms for Data Protection
As threats in the cyber world continue to grow, encryption is still a crucial defense mechanism for securing sensitive information. Here are some additional algorithms you need to know.
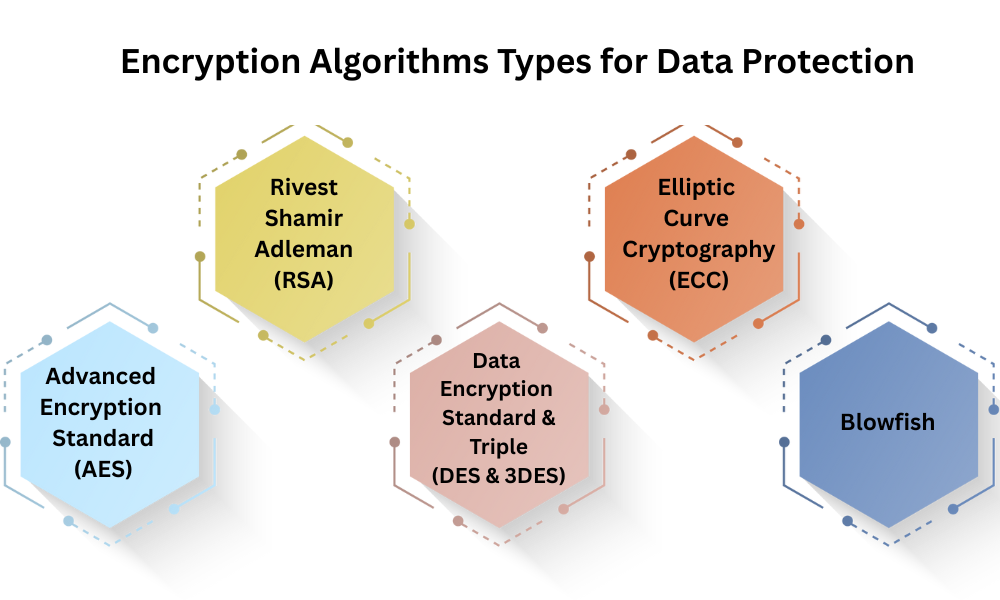
1. AES (Advanced Encryption Standard)
AES is among the most popular symmetric encryption algorithms used throughout government, enterprise, and finance. AES mainly uses block cipher modes with key lengths of 128, 192, or 256 bits and provides very strong security against brute-force attacks. Due to its strong speed and security, it stands as a shield for safeguarding sensitive information.
2. RSA (Rivest–Shamir–Adleman)
Another algorithm is RSA. Public key and decrypting private key is used here. The strength is based on the difficulty of factoring large prime numbers. Digital signatures, SSL/TLS protocols, and secure data transport are common uses for RSA.
Nevertheless, RSA can become sluggish and less effective with high security levels.
3. (Data Encryption Standard (DES) and Triple (3DES)
DES was among the first symmetric encryption standards but is nowadays regarded as insecure because of its short 56-bit key. Triple DES (3DES) was established as a safer alternative, applying the DES cipher three times to every block of data. Though still supported for legacy systems, 3DES is being largely phased out in favor of more secure algorithms such as AES.
4. ECC (Elliptic Curve Cryptography)
ECC is an asymmetric encryption technique that provides the same level of security as RSA but with considerably smaller keys, making it faster and more efficient. It's particularly well suited for mobile devices, IoT applications*, and other environments with constrained computing resources. Because of its short key size, ECC maintains security without compromising performance.
5. Blowfish
Blowfish, designed by Bruce Schneier, is a quick and adaptive symmetric block cipher with key sizes from 32 to 448 bits. This algorithm is available for free and well used in open-source projects.
Benefits of Data Encryption Algorithms
1. Improved Data Protection
Encryption keeps data at rest, in transit, and in use—rendering it invisible to cyber attackers. As attacks such as ransomware and data exfiltration malware continue to grow, it keeps stolen data useless without the decryption key.
2. Secure Cloud Protection
With more and more companies going to the cloud, encryption of cloud data is a must. Though cloud providers encrypt the infrastructure, it is up to the customer to secure data.
3. Compliance with Regulations
Most data privacy laws such as GDPR, HIPAA, and PCI DSS mandate encryption to safeguard financial and personal information. Effective encryption enables organizations to be compliant, prevent penalties, and uphold customer confidence.
4. Data Integrity & Authentication
Cryptographic mechanisms such as hashing algorithms assist in recognizing unwanted alteration or tampering. It confirms your data hasn't been compromised during transmission or storage, ensuring data integrity.
Wrapping it Up
Considering the rise in cyberattacks, encrypting data has become important. In encryption only the authorized user having the decryption key has access to the sensitive data. Thus, chances of your data being stolen or misled are gradually less. Thus, if you are a SMB owner or run a huge business, make sure your data is encrypted.
To stay updated with such relevant security topics, visit us now.
Explore more:
What is Symmetric Encryption? — Definition, Process, and Use Cases
How Does End-to-End Encryption Contribute to Secure Communication?
How the Principle of Least Privilege Benefits Your Data Protection