QR codes and Quick Response Codes today have become the new normal in the digital world. Every day, we buy food items, go shopping, and make payments, through scanners, a.k.a QR codes, that promote contactless interactions. But did you know that scanning QR codes can trick you someday?
Well, if you aren’t aware of it, this blog is for you. Here, we will discuss Quishing, also called QR code phishing, which deceives the user by scanning a malicious QR code. This way, you get into the trap and head over to a malicious website that tries to steal your sensitive information, leading to financial losses, identity thefts, and more.
So, incorporating security practices in the first place can be a savior. In this blog, we’ll first understand QR codes and then provide examples and steps to prevent malicious QR codes.
QR Codes: A Gist
QR, as mentioned above, stands for Quick Response Code and is basically a white square box with white squares, it can easily store URLs, data, and messages. When a user scans the code, it typically takes them to perform a particular action.
This includes opening a website, making digital payments, booking tickets, and more. Even though there are many good sides to QR codes, we cannot ignore the alarming fraudulent activities that may arise due to them. That’s called Quishing, QR Code Phishing.
Knowing About QR Code Phishing
Quishing combines two words, “QR” and “phishing” and is a type of cyberattack wherein the bad actors trick the users with malicious QR codes, aiming to steal sensitive data. As QR codes have become the need of the hour, cybercriminals take advantage to evade conventional security controls.
Unlike conventional phishing that uses email links or imitation websites, quishing conceals the malicious link within a QR code, and the victim has to scan it using their smartphone—usually a less watched-over area by corporate security software.
How Quishing Works?
QR code phishing attacks are more advanced, wherein different methods are used to trick the user.
1. Embedding Malicious Links: Thieves generate QR codes that take users to malicious sites intended to steal login credentials, private data, or financial information.
2. Masking Malware: Certain QR codes trigger the downloading of malicious programs or apps upon scanning. The malware, installed once, can spy on the user, steal data, or infiltrate corporate networks.
3. Fake Payment Portals: Scammers use QR codes to mimic legitimate payment portals, tricking victims into entering credit cards or banking details. This tactic has already been reported in public places like parking meters.
How to Protect Yourself from Quishing Attacks
Below are proactive measures you can take to remain safe:
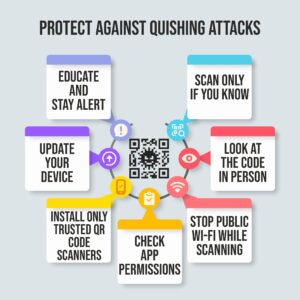
1. Scan Only If You Know
Make sure to scan QR codes only from trusted sources like reputed companies, confirmed websites, or familiar contacts. Don't scan codes in unsolicited emails, adverts, or unknown places.
2. Install Only Trusted QR Code Scanners
Don’t randomly download any QR code app from third-party sources. Make sure to get it only from Google Play or App Store.
3. Look at the Code in Person
Beware of tampered QR codes. Sometimes you may get into the trap with unusual fonts, designs, and more.
4. Stop Public Wi-Fi While Scanning
Do not use public wi-fi when scanning. Consider using the personal network to avoid the man-in-the-middle attack.
5. Update Your Device
Update your OS, applications, and security software periodically. Turn on automatic updates to keep your device secure from known threats.
6. Educate and Stay Alert
Stay updated about new QR code dangers and spread awareness among your employees to instill a culture of vigilance.
7. Check App Permissions
Be wary of QR scanner apps requesting overkill permissions, like contact lists or GPS, if not needed.
Summing it Up
Quishing is a rapidly growing threat that shouldn't be overlooked. Taking prior steps and being aware can keep you away from cyberattacks. The above-mentioned steps can surely help. Staying safe online is all up to you! So, be vigilant and always take the right security measures.
Stay informed and updated with blogs here.
Read More: What is GhostGPT? Will it Enable More Devastating Cyberattacks?