Ask yourself, what do you do when you want a program but don’t have an official license yet? If you have an answer as “surf the net for cracked version” then spoiler alert: this blog is for you. And if your answer was – using the trial variant or looking for a free alternative then you can probably skip this one. Or not!
Sketchy substitute sources are associated with offering cracked editions of software on top of the incentives that they also offer to lure the needy. After soldiering through the ads that are stuffed in the sites you may just get the program that you were looking for, but chances are that it may come with a miner, stealer and obviously without any future updates and the functionality that the network offers.
The appeal of free versions of desired applications can be alluring for cases of small budgets. Here, we will unearth the risks of using unlawful software and the benefits of investing in an authorized program in safeguarding your online presence.
What are Cracked Programs?
Programs or applications that have been modified to get around licensing limitations or application requirements are known as cracked programs. These cracked programs expose users to hefty risks including threats of cybersecurity, legality, and system immutability.
The issue of piracy will not go away; in fact, it is scaling up. Adobe Photoshop is the most looked for cracked versions. It amasses around 50,000 searches monthly for cracked versions. According to Statista, there were 215 billion visitors to pirated websites worldwide in 2022.
How are Cracked Programs Made and Released?
The legitimate software code is altered by the hackers or cybercriminals, or the license mechanism of the software is disabled. The restrictions from this remodeled code are removed and uploaded to various digital file repositories, forums, from where unaware users can download it.
Reverse engineering is applied to inject the bug into the software, which in turn makes it a hazardous tool for spreading malignant programs. Even respected and trusted platforms like GitHub haven’t managed to escape it. Cybercriminals have coaxed platforms like GitHub to distribute malware stuffed cracked programs while deceiving the users who trust the platforms. When downloaded, the software will function as it was supposed to, but the malware secretly installs and starts to access and steal sensitive data like login details, banking credentials and the likes of personal data as well.
The Jeopardy of the Cracked Programs
The risks of using cracked programs go beyond the malware problem. The absence of security updates leaves users wide open to vulnerabilities along with system instability, which is the result of alterations made to dodge the licensing process. This introduces bugs and crashes of the system due to the cracks in the code.
Use of pirated software breaches the laws of intellectual property which exposes users to penalties or even legal action.
When a user downloads pirated software, the potential of exposing your personal information drastically increases. There are apps which store sensitive data like documents, messages, etc. This data can fall into the hands of the wrong people, which can lead to identity theft, financial loss, and harm to the individual or an organization. These programs generally come with spyware which is designed to surveil the user’s online activities. These include – stealing of usernames and passwords, banking credentials, browsing history, emails, photos and videos.
How to Save Yourself from these Cracked Programs?
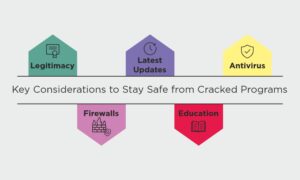
To protect your devices and data from the risks associated with pirated software, it’s crucial to look for a benchmark for cybersecurity.
- Legitimacy – Using legitimate software is recommended. Always get the software from trusted sources. Vendors who are authorized sellers should be preferred.
- Latest updates – You can make sure you have the most recent security fixes and functionality by regularly updating your operating systems and applications.
- Antivirus – Install your system with antivirus solutions which can protect your system against malware.
- Firewalls – The hurdle between potential threats and your device is the firewall. It blocks illegitimate access to the network.
- Education – Being aware of the latest threats in cybersecurity and the best practices to protect yourself from them is essential.
The Impact of Piracy on Businesses and the Future Threats
The consequences of using cracked programs for businesses go way beyond the individual ones. Companies that use illegitimate software put their whole operation and stand in the industry at risk.
Malware can lead to the risk of data breaches of sensitive organization data, which may include customer data, finance records, and intellectual property. Industries generally have strictly regulated compliances concerning data protection and licensing of software. Using pirated software can end in non-compliance and substantial fines. Pirated software is often shaky and subject to crashes, which leads to a decrease in work hours and efficiency. In businesses, reputation is everything. Use of cracked programs can deteriorate trust among customers.
Attackers are smart too; they will try to amend their mistakes and improve their methods of achieving their goals. So, it’s a given that they will pose new challenges. They may use artificial intelligence to build more refined malware, which may advance their reach to different repositories than GitHub and hit them with better cracked programs.
For more informative blogs on cybersecurity and troubleshooting, check out SecureITWorld!
Also Read: Importance of Human Factors in Cybersecurity: Key Takeaways