Digital transformation has contributed to several domains on the grounds of embracing change and development. Doubtlessly, it is the chief element to enhance connectivity and communication beyond borders around the world. Along with the increasing adoption of technology, the need for cybersecurity has risen further. The main reason for such growing requirements of cybersecurity is the unwanted cyber-attacks by online guideline breachers who try to access user data illegally. In simple terms, cybersecurity protects user data from illegal access. Nevertheless, several myths and misbeliefs related to cybersecurity have become popular among people over the years. Therefore, in this article, we will explore the top 10 common cybersecurity myths to highlight the misbeliefs alongside offering measurements to practice cybersecurity better for standard digital experience.
Myth #1: Only IT Professionals are concerned about Cybersecurity
Reality: Everyone should be concerned about it
One of the common myths surrounding cybersecurity is that only IT Professionals should be concerned about it. But the reality is securing digital information should be everyone’s responsibility. Similarly, while working in an organization, every employee has to respect and adhere to cybersecurity guidelines. The reason behind this can be the easy targeting process of the cyber attackers. They find the non-IT workers easier to attack and access their data unlawfully so, understanding such attacks is essential for every individual.
For example, let us assume the finance manager of a tech company is approached by any third-party sources and they grant access to confidential financial information of the other employees due to lack of knowledge. As a result, all the financial data of the company will be available to the cyber attackers who can easily use it for their benefit. Therefore, knowing and practicing cybersecurity is important for everybody irrespective of their professional background.
Myth #2: Small Businesses do not have to care for Cyber Attacks
Reality: Small Businesses are Easy Targets of Cyber Attacks
‘Cybersecurity is not for small companies’ is probably the most prominent myth in contemporary times. Nevertheless, this is a baseless assumption as all the law breakers look for easy targets that they can comfortably tackle. Moreover, minor companies possess basic security guidelines that are certainly breachable by criminals. Alongside, statistics show around 40% of cyber attack victims are small firms. Therefore, it can be said that small firms are the easiest and primary targets of cyber attackers.
Myth #3: Cyber protection is all about strong passwords
Reality: Passwords come with restrictions
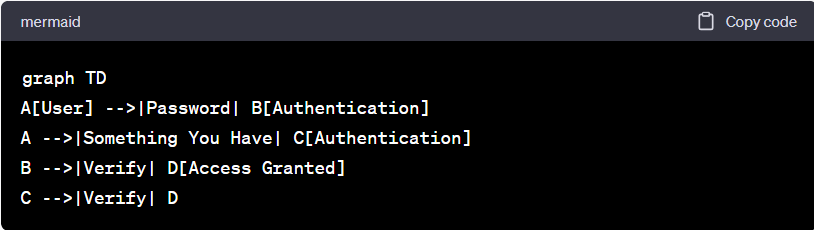
Users doubtlessly have to secure their digital information with strong passwords however, it is not the only element that can save them from cyber attacks. As per various available data, cybercriminals adopt multiple methods to read and break user passwords. Brute force attacks and password spraying are a few techniques to crack passwords. On such grounds, implementing multi-factor authentication (MFA) can be very beneficial. It amalgamates your password, which is something you know with the device you use that is something you have like a smartphone. This process gives additional protection to the digital information. Furthermore, organizations should employ zero-trust architecture to increase the standard of their business data protection methods.
Diagram:
Myth #4: Cyber Attacks can only be observed Online
Reality: Cyber Attacks can take place Offline as well
The misconception of cyber attacks happening only online has justifications as it means illegal access to digitally available information. However, such data breaches can take place offline as well. If cyber attackers get physical access to devices that have sensitive information, they can easily hack it and extract the data illegally. Therefore, along with standardizing cyber security, adopting physical security practices is crucial to restricting cyber attacks.
Myth #5: All Cyber Attacks can be Immediately Noticed
Reality: Some Attacks can go unnoticed
Cyber-attacks do not come with a warning and cannot be identified right away during the time of threat. Cybercriminals follow a stealthy method to breach and access user data so that the owners stay unaware of it. Thus, frequent inspection of systems is important along with implementing illegal trespassing identification techniques.
Myth #6: Antivirus Software gives all the protection from cyber attack
Reality: Antivirus Software comes with restriction
Utilizing antivirus software undoubtedly is part and parcel of cybersecurity practice. However, it cannot give complete protection from cyber-attacks. Its basic responsibility is to identify patterns and signature-based malware. Nevertheless, with rising technological abilities, cyber security breachers are able to bring new types of malware that antivirus software may fail to track. Therefore, antivirus cannot solidify cyber security entirely but its best practices can be accomplished by securing networks, firewalls, etcetera.
Myth #7: Cybersecurity is Costly
Reality: Cybersecurity can be cheaper
Most of us believe that cybersecurity practices are expensive hence refrain from adopting them. But the truth is it can be costly as well as cost-effective. Certainly, the costlier practices are more effective, however, the cheaper ones have also shown quite positive results. Moreover, backing cyber security is a long-term investment that will always provide good returns as cyber-attacks can be excessively expensive. Hence, having a strong password policy, imparting employee education on the subject, and regular software updates are the methods to implement cybersecurity in a more cost-effective way.
Myth #8: Systems are Secured Once they are Patched
Reality: Continuous Patching is important
Similar to utilizing antivirus, patching software usage is also crucial for cybersecurity but cannot provide complete safety from cyber attacks. Cyberlaw breachers are forward and can easily break into third-party systems as well as utilize zero-day vulnerabilities. For this reason, frequent patching updates of the systems are necessary.
Myth #9: Cybersecurity can restrict Access to Information
Reality: There should be a balance between Security and Accessibility
Cybersecurity is mainly about maintaining a balance between data security and accessibility. For example, in an organization, not all employees can access highly confidential data. Data provided to each worker is based on their position. An executive cannot have access to CEO-level information. So, there has to be a balance between the two elements. In this regard, Role-based access control (RBAC) can be very useful to distribute access to the employees of an organization as per their job roles.
Myth #10: The Main Cybersecurity Threats are the hackers
Reality: Human Error and Insider Threats and
Usually, we consider hackers the ultimate threat to cybersecurity ignoring the fact that human errors in an organization can be major challenges to solidify cybersecurity. Human error can take place intentionally and unintentionally. As a result of such mistakes, the firm can be in a devastating situation of cybersecurity breach. For this reason, proper employee training in cybersecurity and tracking their activities is very crucial.
Cyber Threats, a never-ending challenge

The growing requirement for cybersecurity is an indication of the increasing adoption of technology. This growth also encourages cybercrimes to take place. Cyber attacks are happening every now and then breaking the security measures of individuals and organizations. This ultimately contributes to the emerging need for cybersecurity. Hence, in this section, let us discuss the never-ending challenge of cyber threats and give suggestions for fortifying cybersecurity.
The threat of Ransomware Attacks
It is observed that ransomware attacks have been the most common cyber threat in the last few years. In such attacks, attackers encrypt the victim’s data and ask for a ransom to provide the decryption key. This not only can cost high amounts to the victims but also there is a probability of delivering the encrypted data to other parties. Hence, such attacks are considered to be the most impactful cyber threats. To take measures against ransomware:
Best Practice #1: Regular Backups
Regular data backups are important for standardizing cybersecurity. However, such backups have to be done in separate networks or devices to ensure safety from data breaches.
Best Practise #2: Keeping Operating Systems Up to Date
It is essential to keep your software's and operating systems updated. This helps in defending against the cyberattacks, as it enhances existing features, patches security flaws, fix bugging issues and more.
Best Practice #3: Patch Management
Frequent patch updates are important for data security. It helps in staying alert of the vulnerabilities that ransomware may utilize.
The Danger of Phishing Attacks
Phishing is one of the most prevalent cyber-attacks that cyberlaw breakers carry out on companies. During such attacks, attackers usually disguise to be someone else from an organization and send emails to other workers. In emails, criminals ask for confidential information about the organization. Measures to be taken against phishing:
Best Practice #1: Email Filtering
Adopt effective email filtering methods to recognize phishing emails and restrict them from dropping into your co-workers’ mailboxes.
Best Practice #2: Employee Vigilance
Regular employee training on cybersecurity and phishing attacks helps them to identify fraudulent emails. This further assists them to understand what to do after receiving such emails.
Best Practice #3: Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a superior way to prevent cyber attacks like phishing. This method makes it challenging for cybercriminals to attain login credentials of the users and break into their systems.
The Threat of Insider Attacks is Growing
Intentional or unintentional, any type of insider attack is dangerous for any organization. Hence, giving access to confidential information to employees can be problematic as it can be compromised at any time. Safety measures against insider threats:
Best Practice #1: Access Controls
Follow a strict access control methodology. Not every employee requires confidential information from a company. So, making the access procedure strict will help in giving data access to the employees as per their job roles and requirements.
Best Practice #2: Monitoring and Audit Trails
Monitoring and maintaining audit trials will not only standardize cybersecurity practices but also highlight unauthorized or illegal access to protected data.
Best Practice #3: Employee Training
Never miss a chance to train the employees on cybersecurity. This enhances their knowledge of the subject teaching the methods to handle any crisis situation.
Zero-Day Vulnerabilities can be major challenges
Zero-day vulnerabilities are the shortcomings or weaknesses present in the software and hardware of a system that can be easily identified and exploited by cyber attackers while under cyber attack. It simply weakens the cyber defense to access user data illegally. Mitigate zero-day vulnerabilities with:
Best Practice #1: Vulnerability Scanning
Frequent scanning and evaluating systems can help in identifying vulnerabilities. Measures to manage and tackle such elements can be done accordingly.
Best Practice #2: Network Segmentation
Segmenting network and data can help immensely as distributing it among the employees will be easier as per their role. This can reduce data breaches by a margin.
Best Practice #3: Threat Intelligence
Threat intelligence technologies allow users to identify vulnerabilities and any unwanted activities concerning sensitive data.
How to Build a Robust Cybersecurity Strategy?
Along with the advancement in digital transformation, cybersecurity should also progress to provide flawless digital experience to users. While constructing a robust cybersecurity strategy, consider the below-mentioned factors
Best Practice #1: Continuous Security Training
Unawareness about cybersecurity is the biggest challenge in the process of practicing it in the best way. Therefore, aware your employees about the subject through regular training. Make it compulsory for every employee starting from executives to managers for better outcomes against cybercrimes.
Best Practice #2: Incident Response Plan
Constructing an incident response plan will help in imparting knowledge about the steps to be taken if any incident related to security breaches takes place. This will further assist in mitigating the approaching risks strategically.
Best Practice #3: Security Audits and Penetration Testing
Frequent security audits and penetration testing allow companies to recognize the weaknesses in their cybersecurity practice and take measures to address those factors.
Best Practice #4: Collaborate with Cybersecurity Experts
Collaboration with experts is a great way to identify the flaws within the ongoing cybersecurity practices and employ highly efficient methods against cyber threats.
Best Practice #5: Data Encryption
Adding robust encryption to sensitive data is similar to adding an additional protection layer to it. This helps in keeping cybercriminals away from data breaches.
Best Practice #6: Regulatory Compliance
Adhering to cyber regulations adds to the company's reputation. Breaching it can bring unwanted consequences. So, stay aware of the ongoing regulations in cybersecurity and comply with them for better outcomes.
The Future of Cybersecurity

The cybersecurity landscape is doubtlessly evolving and has a positive scope for development in the upcoming years. With each technological innovation, cybersecurity will observe a high demand to protect user data from illegal access. The following are the ongoing trends to look out for in the field of cybersecurity:
Artificial Intelligence (AI) in Cybersecurity
AI is expected to be a crucial segment of cybersecurity in terms of recognizing and tackling cyber threats. The algorithms in this technology bear the capability of storing and scrutinizing big data. Hence, its contribution to cybersecurity can be immense in the following years.
Internet of Things (IoT) Security
The increasing usage of IoT in our day-to-day lives is an indication that it has a major role to play in cybersecurity. As our sensitive information is available in IoT devices thus, protecting such devices should be our priority while taking steps against cyber threats.
Quantum Computing Threats
The innovation of quantum computing has offered several advantages and disadvantages lately. It has the ability to break strong password encryptions in our systems easily. So, it can become a significant aspect of cybersecurity in the upcoming years.
Blockchain for Security
Blockchain methodology allows us to make transactions safely and securely. It provides transparency while showing transaction history helping in keeping track of our financial activities.
Enhanced Cloud Security
Cloud services allow us to store huge amounts of data safely. As the usage of such services increases, the probability of threats and attacks also increases. Therefore, securing cloud storage can be a vital part of cybersecurity in upcoming years.
Conclusion
Technological advancement is ever-evolving and is rapidly changing with each new innovation. This specifies how fast we are adopting these digital transformations. Such rapid adoption enhances the need for cybersecurity even further. The best way to address cyber threats is to stay informed and inform others about such attacks as well as the methods to mitigate their impact. Moreover, while working in an organization, we have to make sure that cybersecurity is an individual responsibility of each employee. Therefore, everybody should be aware of the basics of cybersecurity to safeguard user data and eliminate the risks of cyber attacks. This not only allows us to utilize digitalization flawlessly but also keeps cyberlaw breakers away from your confidential data. Collaborate with SecureITWorld to experience advanced cybersecurity practices and progress technologically keeping the worries of cyber attacks aside.
Read More:
Comprehensive Mobile Device Security: Safeguarding Your Digital Life





