Ransomware attacks are one of the high-profile cyber attacks that occur worldwide, chiefly targeting companies. Organizations consider it the most devastating threat. Stats define that-
- The average ransomware attack in 2023 is $1.54 million, double the 2022 figure of $812,380.
- As of 2023, the ransom attack affected over 72% of businesses worldwide.
- There has been a rapid rise of 13% in the last five years in ransomware attacks, with an average cost of $1.85 million for every incident.
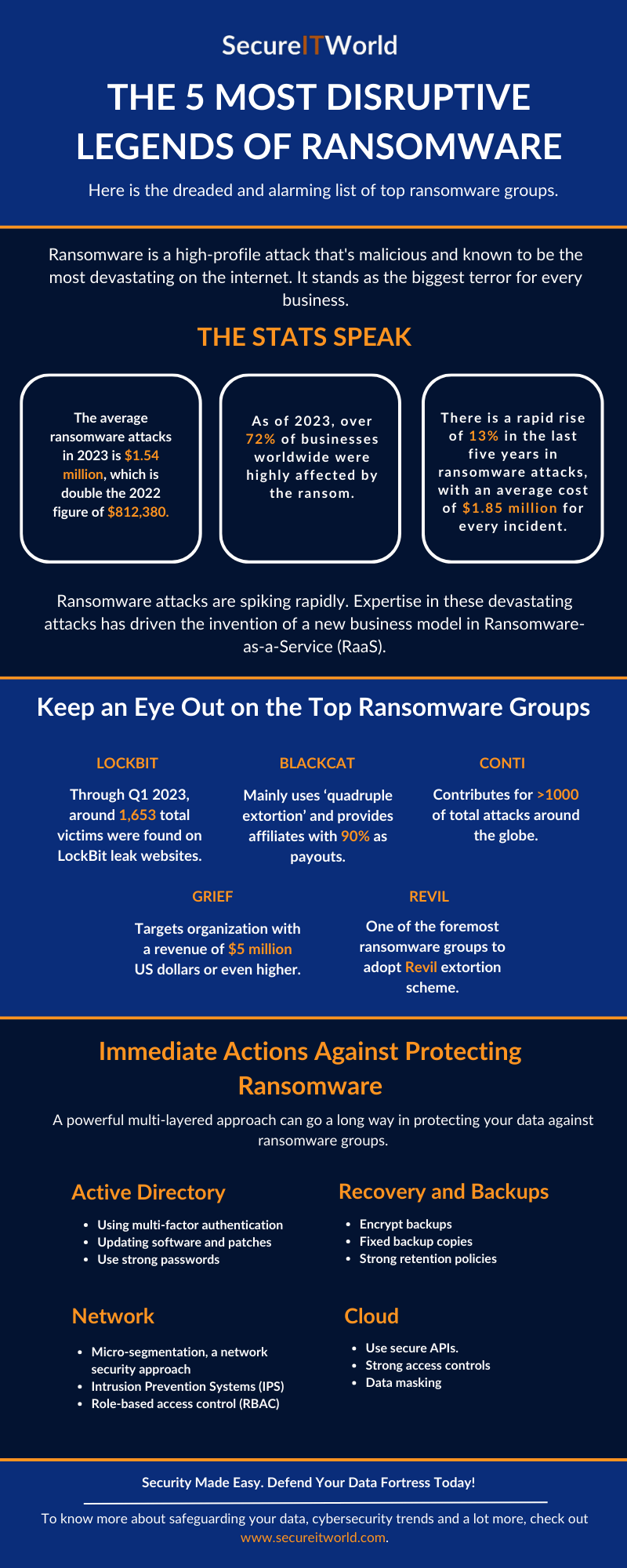
The Most Popular Ransomware Groups Are:
LockBit: By the first quarter of 2023, over 1654 ransomware victims were identified on the leaked LockBit website.
Blackcat: It utilizes the method of quadruple extortion to offer 90% of payouts to its affiliates.
Conti: It has been responsible for around 1000 ransomware cases globally.
Grief: It targets organizations with a revenue of $5 million or more than that.
Revil: It practices the Revil Extortion Scheme to carry out ransomware attacks.
Methods to Mitigate Ransomware Attacks:
- Adopt a multi-layer security approach with multi-factor authentication
- Regularly update software and use strong passwords.
- Create backups, and do not forget to encrypt those
- Adopt a micro-segment approach in the network
- Implement robust access control with secured APIs
- Do not forget to practice data masking
Also Read
Mastering Cybersecurity in 2024: Navigating the Ever-Evolving Landscape
